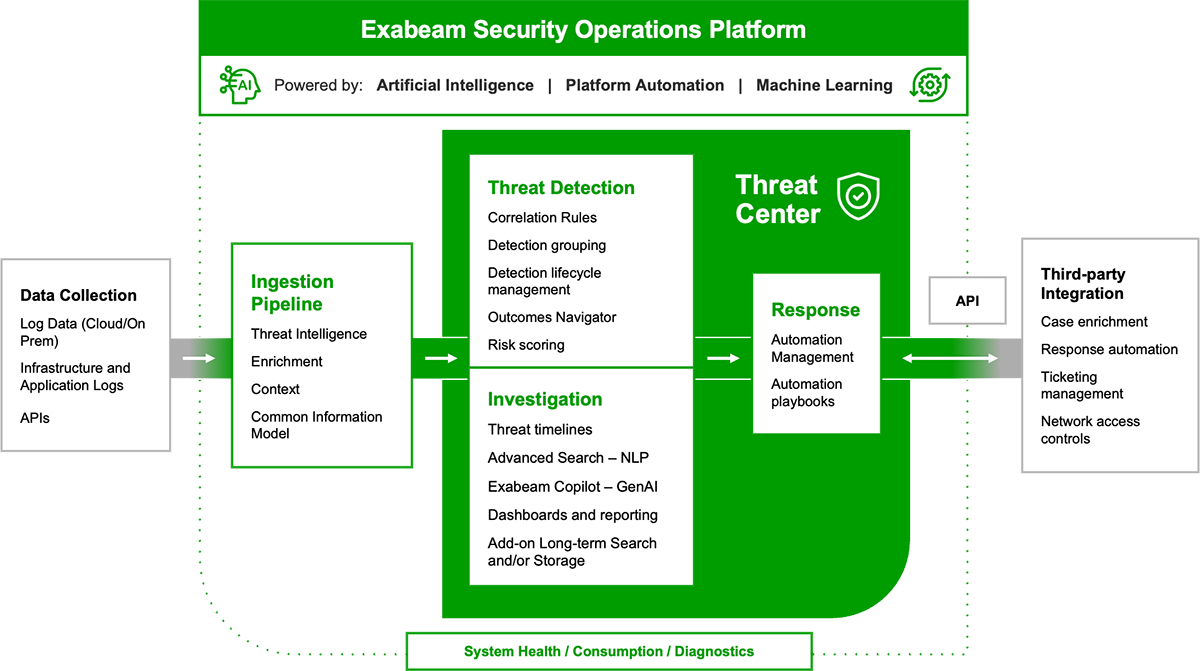
The Exabeam Security Operations Platform
The AI-driven Security Operations Platform for faster, more accurate threat detection, investigation and response
It’s Time for a New Approach
An AI-driven Security Operations Platform: The Basics
The Exabeam Security Operations Platform combats cyberthreats by applying AI and automation to security operations workflows, delivering effective threat detection, investigation, and response (TDIR). AI-driven detection pinpoints high-risk threats by learning normal behavior of users and devices, and prioritizing threats with context-aware risk scoring for faster, more accurate, and consistent TDIR.
Augment security tools with a modular, open platform that applies AI and automation to maximize investments with connected insights and integrated workflows.

Data Collection
Collect data from on-premises or cloud data sources from 200+ on-premises products, 34 cloud-delivered security products, 11 SaaS productivity applications, and 21 cloud infrastructure products from the three leading cloud infrastructure providers.
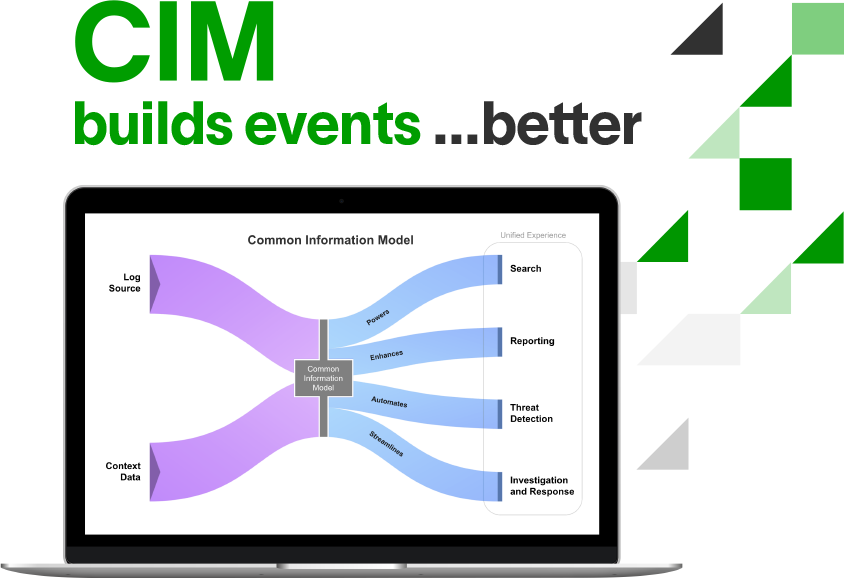
Security Data Preparation and Organization
Exabeam built a Common Information Model (CIM) to provide normalized, security-relevant logs that are faster and easier to parse, store, and manage from any vendor. The CIM schema simplifies the normalization, categorization, and transformation of raw log data into actionable events in support of security use cases. The CIM defines the 10 most important fields and 76 subjects used by security experts and specifies them as core, detection, or informational, and includes 395 activity types and two outcomes (specified as success or fail). This process allows organizations to more quickly detect and respond to threats, visualize and report on data, and supports lightning-fast search performance.

Compliance and Certifications
Running national and global organizations means you need to comply with laws around the world, and Exabeam can help you meet your compliance requirements. Exabeam achieved ISO 27001:2017:2018 certification, SOC 2 Type II certification, is registered and certified with Privacy Shield, has appropriate technical and organizational measures in place for GDPR, and has resources available to help you address commitments to your own customers and their personal data. Exabeam has been independently assessed by an IRAP Assessor at the Protected level.
The governance team at Exabeam is dedicated to maintaining a secure operating environment for your confidential data. A zero trust internal policy, ongoing security awareness training, and regular third-party security assessments are just a few of the ways Exabeam helps ensure the security of our customers.
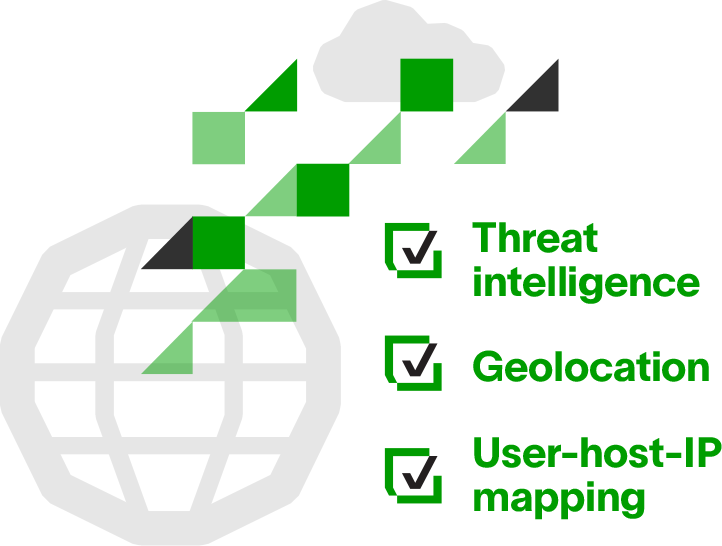
Security Context Enrichment
Context enrichment provides powerful benefits across several areas of the platform. Exabeam supports enrichment using three methods: threat intelligence, geolocation, and user-host-IP mapping. Armed with the most up-to-date IoCs, our Threat Intelligence Service adds enrichments such as file, domain, IP, URL reputation, and TOR endpoint identification to prioritize or update existing correlations and behavioral models. Geolocation enrichment provides location-based context often not present in logs. Outside of authentication sources, user information is rarely present in logs — Exabeam’s user-host-IP mapping enrichment adds user details to logs which are critical to building behavioral models for detecting anomalous activity.

Data Ingestion and Parsing
A new feature, Log Stream, delivers rapid log ingestion processing at a sustained rate of over 2M EPS. A central console enables you to visualize, create, deploy, and monitor parsers within a unified ingestion pipeline for all Exabeam products and features. As it is ingested, data is parsed using 9,500+ pre-built log parsers and enriched using context sources from open source and commercial threat intelligence feeds. Live Tail capabilities provide self-service, real-time monitoring of parser performance, and visibility into the data pipeline, allowing organizations the ability to take immediate action to improve the quality of data ingestion.
MITRE ATT&CK® Coverage
The Exabeam Security Operations Platform uses the ATT&CK framework as a critical lens to help improve the visibility of your security posture. Support for ATT&CK framework spans all 14 categories, including 199 techniques and 379 sub-techniques.


Use Case Outcome Analysis
The Outcomes Navigator feature maps the feeds that come into the Exabeam platform against the most common security use cases and suggests ways to improve coverage. Outcomes Navigator supports measurable, continuous improvement focusing on outcomes by recommending information, event stream, and parsing configuration changes to close any gaps.
Correlation Rule Building
Correlation rules compare incoming events with predefined relationships between entities to identify and escalate anomalies. The Exabeam Correlation Rule Builder feature is a single interface that lets you write, test, publish, and monitor custom correlation rules for your most critical business entities and assets, including defining higher criticality rules for advanced threats sourced from the Threat Intelligence Service (available at no additional cost).
Properly designed correlation rules enable enterprises to surface a broad range of abnormal behavior and events. Correlation Rule Builder provides analysts with an easy application to create custom correlation rules suited to their organization’s security and use case requirements. Correlation rules monitor for well-known threats, identify compliance violations, and detect signature-based threats using context from the Threat Intelligence Service or other third-party threat intelligence.

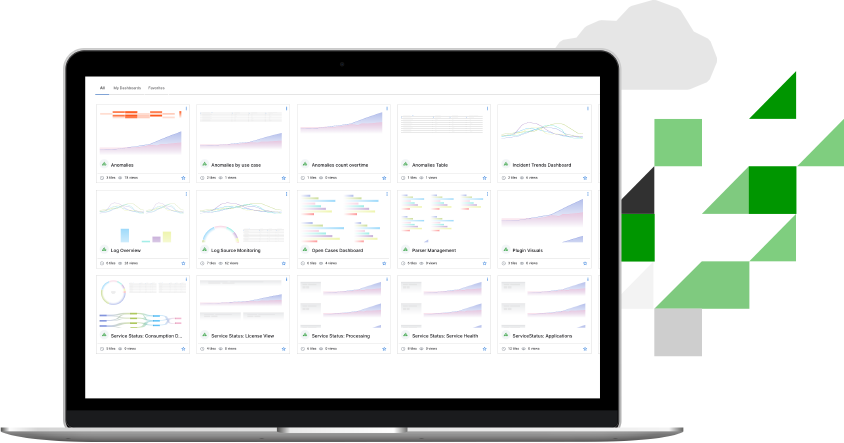
Reporting and Dashboards
Print, export, or view dashboard data with over 45 pre-built compliance reports, case management reports, or build a dashboard in a minute based on a Correlation Rule or Search output as if you were using a leading BI tool. Customers can choose one or more visuals to meet their business needs. These include bar chart, column chart, line graph, area chart, pie chart, donut chart, bubble chart, funnel, single value, sankey map, heat map, table, and Coverage Map.
Threat Intelligence Context
Available in all Exabeam products at no additional cost, the Threat Intelligence Service adds context enrichment to events from multiple commercial and open source threat intelligence feeds, then aggregates, scrubs, and ranks them, using proprietary machine learning algorithms to produce a highly accurate, up-to-date stream of IoCs. The threat intelligence data is refreshed every 24 hours and leveraged by all Exabeam products.

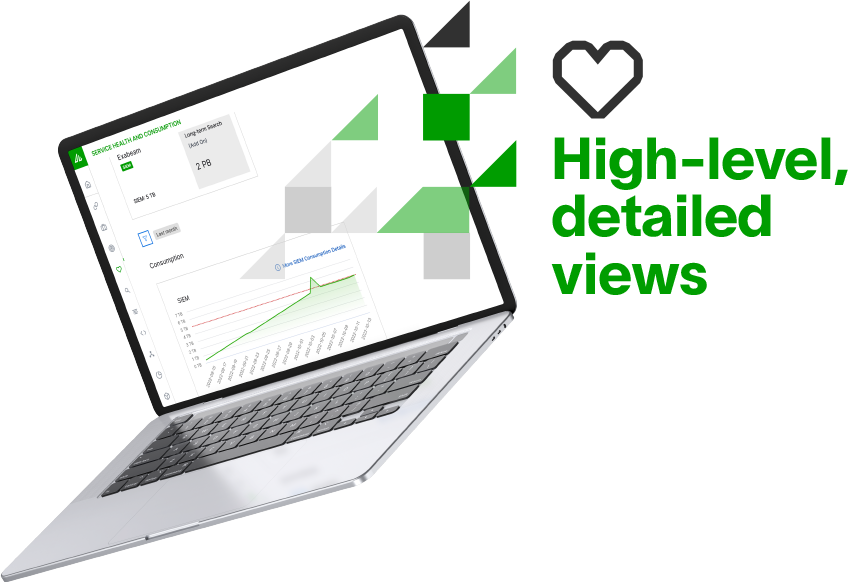
Service Health and License Consumption
The Service Health and Consumption feature provides high-level and detailed views of the health and data consumption performance of your Exabeam service. Visualize your service health and data consumption while monitoring your connections and sources. Monitoring visualizations makes it easy to understand the current state of your Exabeam implementation. The performance component illustrates how your data contributes to overall license consumption and highlights significant changes.
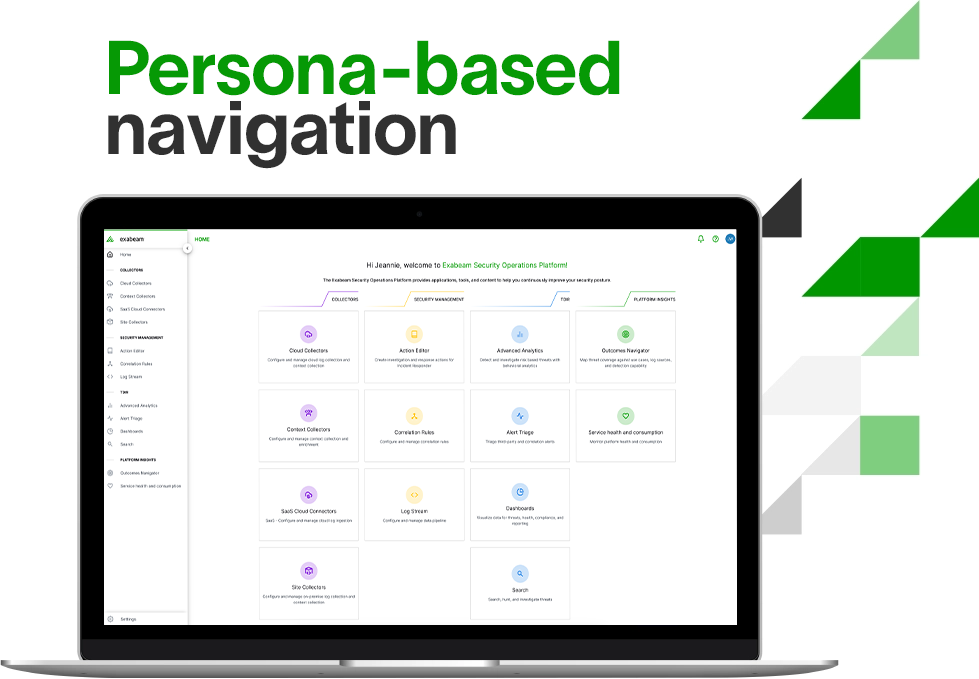
Navigation Center
Navigate your Exabeam applications quickly and easily. The Navigation Center offers simple persona-based navigation with access to the applications you need to accomplish your everyday tasks. All your Exabeam applications will be displayed alphabetically and organized into the following categories: collection, security management, TDIR, and platform insights. The matching navigation bar can be pinned for fast application switching during your daily routine.
integrations
Collect data from more than 680 different product integrations across 350+ different vendors.
pre-built compliance dashboards
Build a dashboard in a minute from 14 different pre-built chart types as if you were using a leading BI tool.
MITRE ATT&CK® categories
Coverage for all ATT&CK categories, including 199 techniques and 379 sub-techniques.
Frequently Asked Questions
Answer: Yes. As customer demand increases either due to a temporary spike in usage or normal customer growth over time, we leverage the elasticity of the cloud to add the necessary, incremental resources to meet that demand through auto-provisioning. In addition, we monitor hundreds of metrics for every service location to ensure availability.
Answer: Exabeam cloud-native solutions receive data from Collectors over the network or internet link through approved ports/protocols documented here. Collectors minimize the impact on the network through compression, batching, and local buffering to gracefully work in congested networks.
Answer: Exabeam delivers updates and feature rollouts continuously on our cloud platform. Updates are immediately available to Exabeam Security Operations Platform customers.
We ensure the highest quality of all our feature rollouts by implementing proactive controls including:
Early access and beta customer program – Our beta program allows customers to try pre-release features. If you are interested in accessing a beta release, please contact [email protected].
Secure code development training – Regular security and code development training and rigorous process requirements arm our employees with the knowledge and support they need to keep all of our sensitive customer data safe.
Static code analysis – We have facilitated security hardening during development by implementing processes to identify, triage, and remediate vulnerabilities.
Internal penetration testing – We conduct regular internal penetration tests to gauge network vulnerability and incident response.
Third-party external penetration testing – We also conduct unscheduled pen tests by third-party organizations to review common techniques, tools, and procedures used by external threat actors.
Trusted by organizations
around the world





















“Using Exabeam reminded me of how surprisingly fast the platform updates. There is an almost daily improvement on desired functions, and with Exabeam, it all keeps getting better.”
Keisuke Kawakami
Infrastructure System Division | MTI Ltd.

Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.

DATA SHEET
The Exabeam Security Operations Platform
Whether you replace a legacy product with a New-Scale SIEM, or complement an ineffective SIEM solution by adding the industry’s most powerful user and entity behavior analytics (UEBA) and automation to it, the Exabeam Security Operations Platform can help you achieve security operations success.

WHITE PAPER
Keys to the Kingdom: Guidance for Effective Zero Trust Architecture
In the event of a security breach, the cost to your organization can be tremendous in terms of both reputation and money. This paper attempts to resolve the confusion surrounding Zero Trust Architecture (ZTA), and presents a strategy to fill in the gaps exploited by malicious insiders and credential-based attacks

WEBINAR
Introducing Exabeam Fusion: The Industry’s Most Powerful and Advanced Cloud-native SIEM
Whether it’s phishing, ransomware, malware, or lateral movement, accessing valid credentials is the adversaries’ primary objective. Exabeam Fusion represents the industry’s most powerful and advanced cloud-native SIEM.
What else can Exabeam do for you?
At Exabeam, we deliver persona-based workflows, purpose-built for security. With support resources, professional services, training opportunities, and business partnerships, Exabeam can usher your organization through deployment and beyond.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision









