Powerful Behavioral Analytics
Behavioral analytics baseline the normal behavior of users and devices with histograms, to detect, prioritize, and respond to anomalies based on risk.
Baseline user and device behavior
Exabeam offers industry-leading user and entity behavior analytics (UEBA) that baselines the normal behavior of users and devices with histograms to detect, prioritize, and respond to anomalies based on risk. Understanding normal allows you to detect the behaviors missed by other tools, such as lateral movement, privilege escalation, credential swapping, and more.


Advanced Analytics
The Advanced Analytics feature offers over 1,800 detection rules and 750-plus behavioral models to baseline normal behavior and identify anomalies and threats, such as credential-based attacks, lateral movement, and ransomware activity.
To understand normal behavior and detect anomalies as normal keeps changing, all user and device activities get baselined. Risk-based prioritization uses machine learning to automatically assign risk scores to all events, prioritizing triage, investigation, and response for key incidents and automatically visualizing these events within Smart TimelinesTM that show full event flows and activities to inform the next right action. Smart Timelines help detect lateral movement by organizing incidents to follow attack activity, credentials use, or permission changes within your environment. This enables you to find and address the threats others tools miss, uplevel your security team speed and performance, and stay ahead of your adversaries.
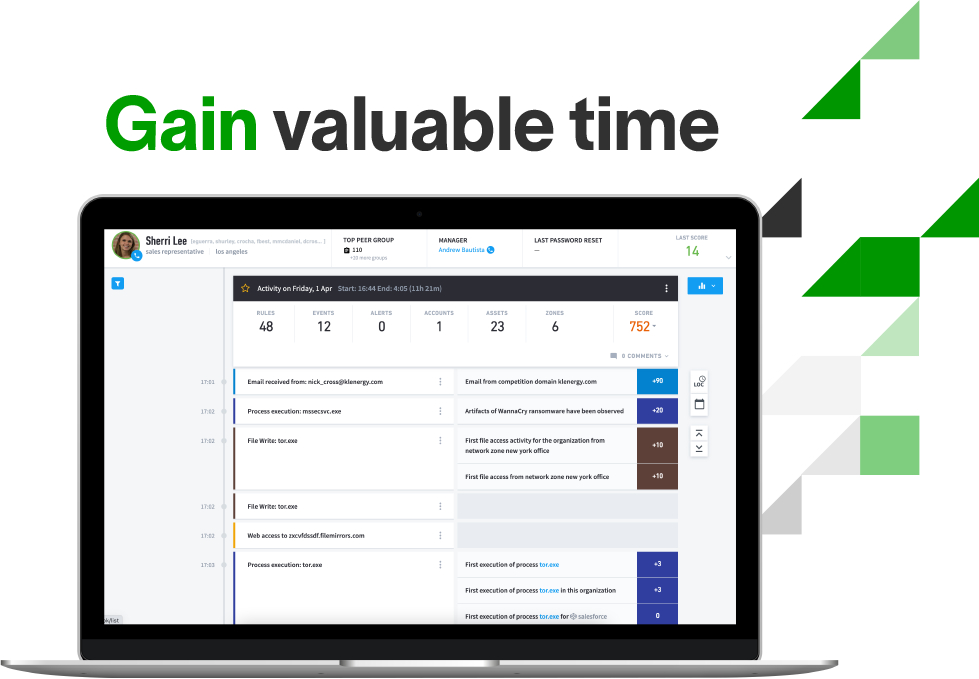
Smart Timelines
Exabeam baselines normal activity for all users and entities, sorting all notable events visually and chronologically within an automated Smart Timeline. The timeline conveys the complete history of an incident and scores the risk associated with each event, saving an analyst from writing hundreds of queries.

Dynamic Alert Prioritization
Dynamic Alert Prioritization applies machine learning to automate third-party alert prioritization by infusing third-party security events with context from UEBA to dynamically identify, prioritize, and escalate the alerts which require the most attention. Classifying alerts provides a starting point for the analyst to begin the triage process, focusing human time and resources on the alerts of highest risk to the organization.
Anomaly Search
Anomaly Search is a simplified search experience for Exabeam-triggered events across the data repository. It offers a drop-down menu for easy query construction against the list of events to determine and declare incidents. Anomaly Search pairs behavior-based TTP detection with known indicators of compromise (IoCs) to enhance an analyst’s threat hunting capability. The solution provides a flexible search capability across a variety of different objects, such as sessions, rules, users, assets, MITRE TTPs, anomaly identification, and cases.

of breaches
Percentage of breaches involving compromised credentials.
MITRE ATT&CK® categories
Coverage for all ATT&CK categories, including 199 techniques and 379 sub-techniques.
anomaly rules
Over 1,800 anomaly rules, including cloud infrastructure security, with over 795 behavioral models that automatically baseline normal behavior of users and devices.
Frequently Asked Questions
Answer: Exabeam has the ability to follow attacks if they move laterally by way of changing devices, IP addresses, or credentials by presenting the entire attack chain without any gaps or missing pieces where lateral movement occurred.
Answer: Dynamic Peer Grouping uses machine learning to assign users to groups based on their behavior, and then compares their activity against the behavior of those groups with the goal of identifying anomalous, risky activity. Dynamic peer grouping is able to augment data in Active Directory and can group users based on any common interaction with the IT system, for example a commonly used application, office location, manager, and more.
Answer: Exabeam automates the prioritization of third-party security alerts and Exabeam triggered alerts with machine learning that understands the rarity of an alert, how often it was fired, among other factors. Exabeam then classifies alerts by priority levels to help discover which alerts are most critical to an organization and need to be reviewed first.
Trusted by organizations
around the world





















“The alerts we’re seeing are not coming out of there because it’s defined use cases, but rather from the behavioral aspects, this is something that we wouldn’t catch with traditional solutions.”
Christophe Rome
Chief Information Security Officer | Lineas

Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
What else can Exabeam do for you?
At Exabeam, we deliver persona-based workflows, purpose-built for security. With support resources, professional services, training opportunities, and business partnerships, Exabeam can usher your organization through deployment and beyond.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision










