10 Must-Have Features to be a Modern SIEM
Legacy security information and event management (SIEM) systems first became available in the nineties and were adopted by security operations centers because of their promise to provide insights into the deep, dark corners of their networks. Information security teams needed to see when and where security threats were happening, investigate those events, and make decisions on the appropriate response.
However, the first generations of SIEMs required expert data analysis and a skilled team able to filter out the growing avalanche of noisy alert sources to discover the real security threats.
Because of the labor-intensive processes, incomplete log sources, and expert skills needed, meaningful but innocuous events could be missed while investigating incidents typically would take weeks (or even months) to uncover and investigate — and breaches then took that much longer to mitigate.
That was then — modern SIEM is now
Modern SIEMs can now apply new features to your security domain that weren’t available with legacy SIEMs. Many SIEMs claim to be “next-generation,” and yet don’t have the features and functionality needed to solve the problems most security teams face today.
What features are needed to be a modern SIEM?
Because legacy SIEMs and current network topologies spanning local, cloud, and remote assets and users, security analysts are facing a very high signal-to-noise ratio. In many cases SIEMs have become relegated to looking at high criticality events and satisfying compliance requirements — and not much else.
Here are the features needed in a modern SIEM solution—combining the latest technology with a comprehensive knowledge of how threats emerge:
1. Collect and manage data from all available sources
Present-day threats typically span multiple data sources. To be effective, every data source must be available to your modern SIEM for it to analyze and correlate the data. (See Figure 1.) This includes cloud service data, on-premises log data (security controls like identity, databases, and application logs), and network data (intrusion detection, endpoint, flows, packets, etc.)
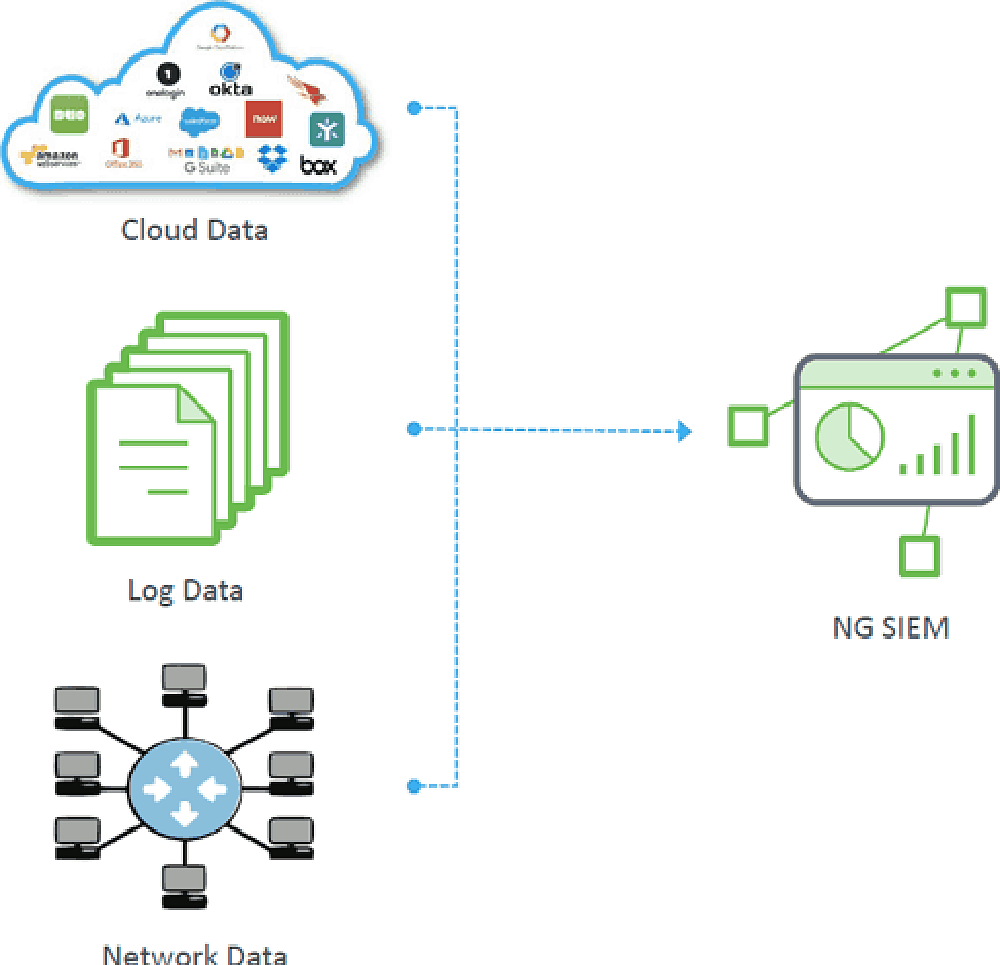
Your SIEM should also include centralized, remote security data management. After you have all log collectors configured and running, it should be easy to manage them (start, stop, update, reconfigure) from any location. Outcomes navigator stuff here.
2. Well-vetted, big data architecture
Many legacy SIEMs were architected in the early 2000s and use proprietary technology. There is a significant technological difference between then and now. Platforms such as Hadoop, Mongo, Elasticsearch, BigQuery, and Spark simply weren’t available then.
With the explosion of security data available and being collected, what’s now needed is a big data architecture that can scale data, pivot within it, and take advantage of advanced data science algorithms for fast queries and visualization.
3. Predictable pricing for log ingestion
Log retention settings are crucial as they enable optimized spending by automatically removing unnecessary logs. By defining a specific time period to retain individual logs by type and source, organizations can free up storage capacity, ensuring predictable spending. Unneeded logs are purged, preventing the accumulation of excessive data and associated storage costs.
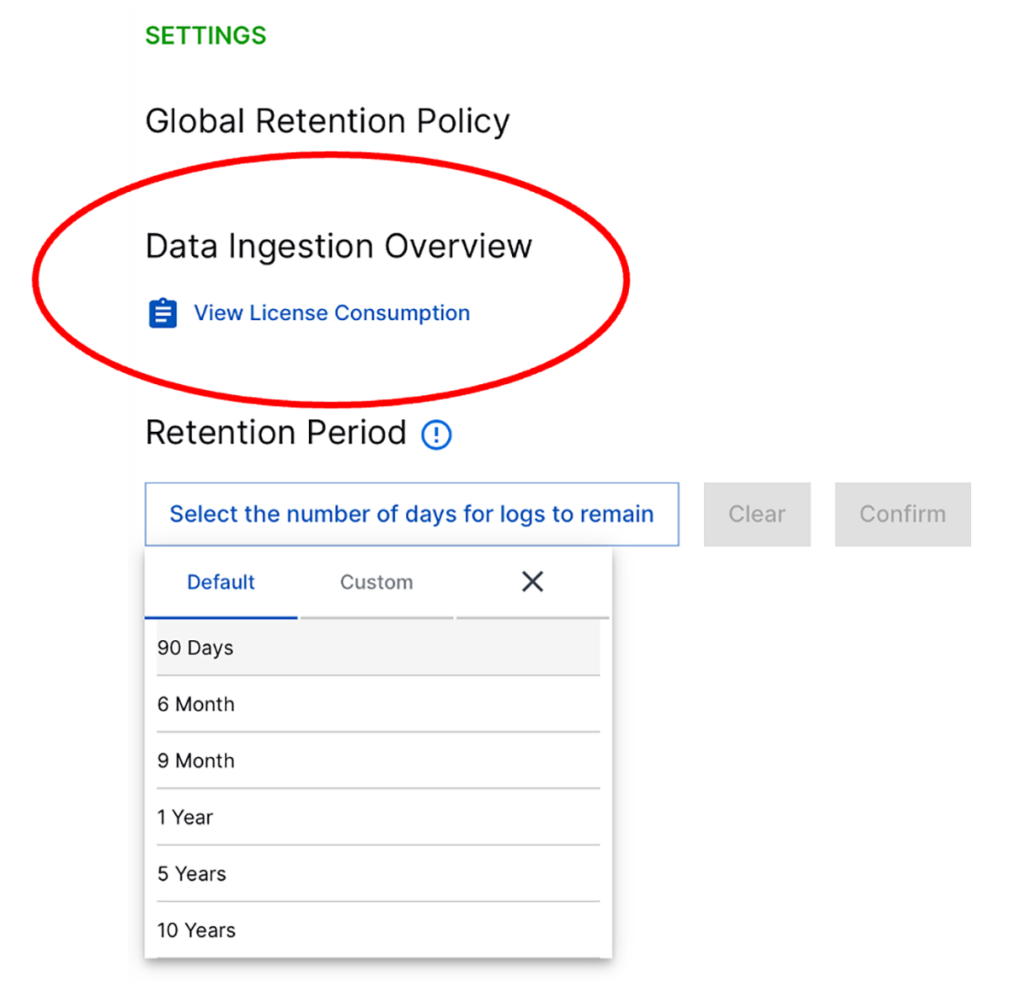
For example, replacing your firewall with an updated model might increase logging tenfold. With consumption-based pricing, your SIEM license fees automatically increase. But with a flat-rate pricing model, you can ingest data from all sources (instead of cherry-picking) and remain within your budget.
4. Enrichment of user and asset context
Look for a high level of enrichment that yields useful results from all the data you’re collecting. Advances in data science provide many insights that previously had to be correlated by experienced analysts, such as:
- Free threat intelligence integration and correlation
- Dynamic peer grouping
- Associating IP addresses with user credentials, devices, and timelines
- Tracking asset ownership
- Associating user and machine types with activities
- Identifying service accounts
- Correlating personal email addresses with employees
- Associating badging station log activity with user accounts and timelines
By using a SIEM that understands context and intent, you can look up asset ownership, user login location, peer groups, and other information that can help you discover abnormal behaviors.
5. User and Entity Behavior Analysis
A modern SIEM automatically baselines behavior through machine learning, statistical analysis, and behavioral modeling—referred to as user and behavior analytics (UEBA).
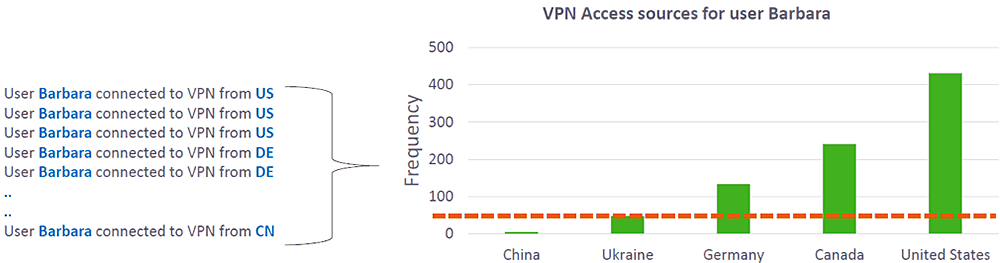
Once UEBA assesses normal behavior, it can assign risk scores to unusual activity, and expose activities and behaviors that exceed a specified threshold. For example, if you have a user who usually logs in from the US, and now logs in from China for the first time, such an anomaly might be indicative of an attack in progress.
6. Automated tracking of lateral movement
By studying past incidents and looking at the MITRE ATT&CK framework, we know that over 80 percent of attacks involve lateral movement. This is where attackers attempt to evade detection or gain access to higher privileges by changing credentials, escalating privileges, then moving to high-value IP addresses and assets. To effectively follow lateral movements from beginning to end, your SIEM must be able to tie such related events from different log sources together.
7. Improved security information model
Legacy SIEMs have a security model that’s mostly based on discrete events. Manually converting an event series into a structured behavior timeline requires a huge amount of time. For advanced analysis, security data must be stored in a useful form factor—for example, a timeline that contains the entire scope of each user and entity you’re monitoring. When all required information is organized in this way, expert systems immediately provide their complete context when surfacing abnormal events.
8. Prebuilt incident timelines
Using a legacy SIEM usually requires a combination of complex queries, followed by a lot of copying and pasting from each source to a common file (often using a text editor as a repository). Such investigations require huge amounts of time, deep security domain expertise, mastery of query languages, and the ability to interpret results. These skills are both expensive and in short supply.
With an abundance of enriched data in a suitable information model, a modern SIEM can present all available context in a concise and friendly UI—the single pane of glass.
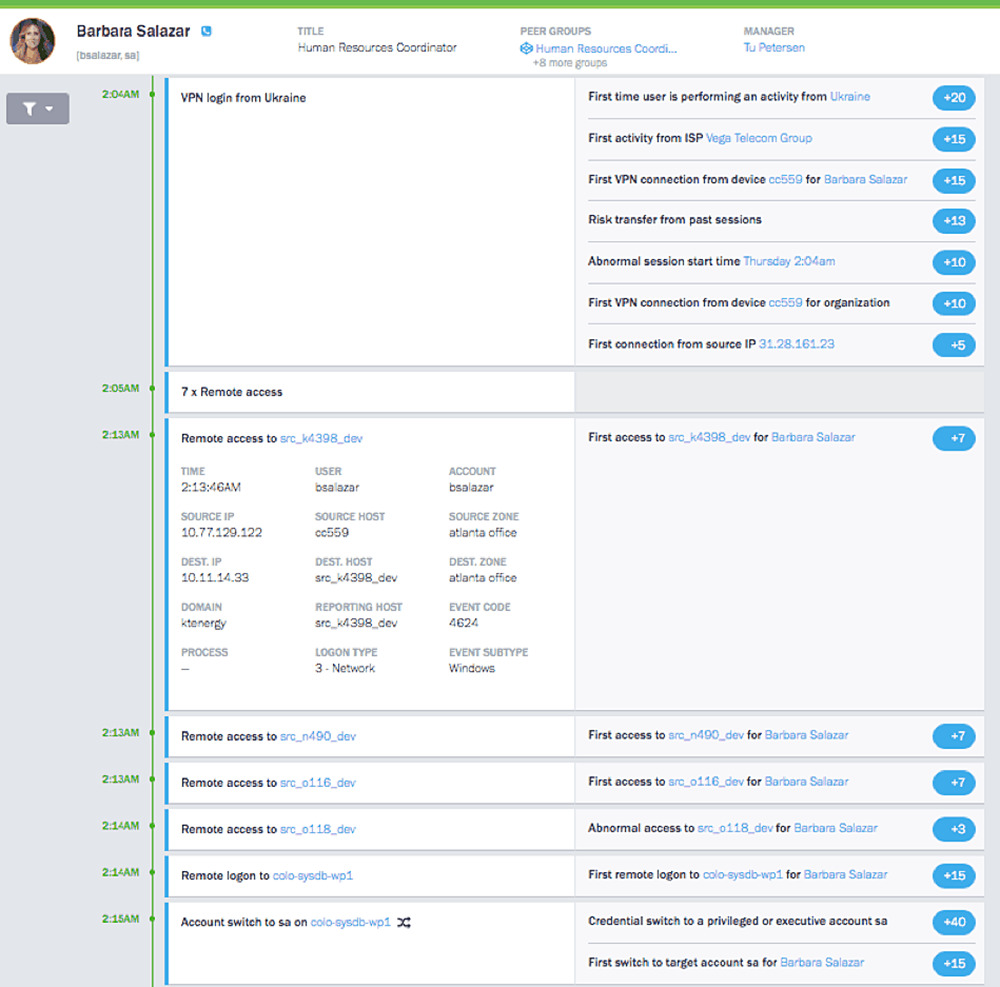
9. Incident prioritization
The amount of data SOCs need to analyze is staggering. It’s not unusual for large companies to generate hundreds of millions of log entries every day.
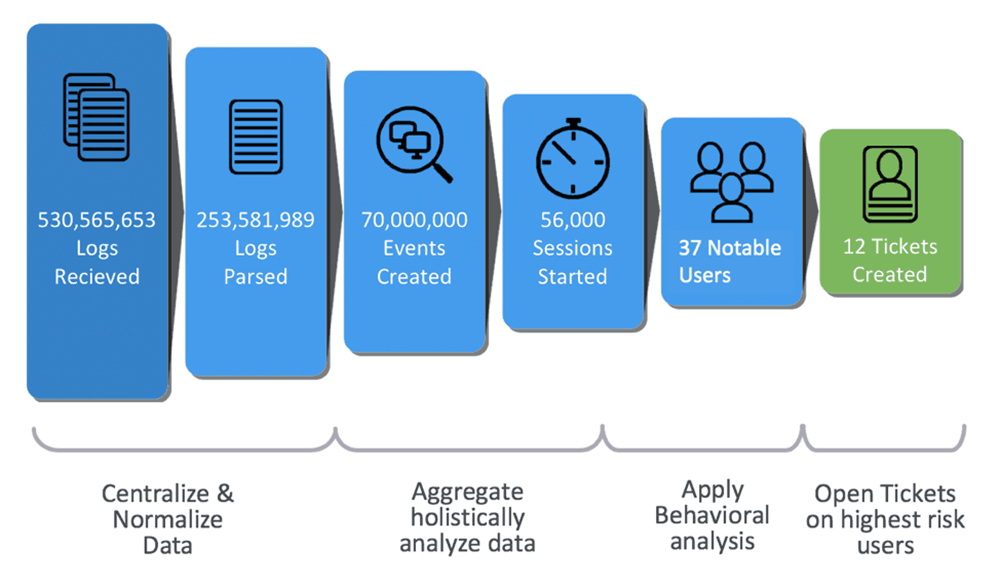
Modern SIEMs are designed to reduce the signal-to-noise ratio to where you can regain domain control. The ability to eliminate false positives and focus only on events with abnormal behaviors is essential for robust security, efficient staff performance, and keeping down costs.
On a typical day, a best-in-class SIEM solution might reduce 500 million log entries to 60,000 session timelines, then surface fewer than 50 notable events. From these, a dozen or so tickets might be generated for investigation.
10. Automation across the TDIR workflow
SIEM vendors use different abbreviations for this capability, which includes two key areas:
Automation
- Using response playbooks to codify best responses to specific threat types
- Providing workflow automation on top of your orchestration plumbing
- Enabling threat response automation, while also reducing personnel tedium
- The ability to control all your tools from one place
Orchestration
- Deploying prebuilt connectors to your IT and security infrastructure, without having to script them yourself
- Easily pull/push data into/out of your access management systems, firewalls, email servers, network access controllers, and other management tools
An advanced SOAR solution can free up your highly skilled analysts to create playbooks, while enabling junior analysts to run them. You can realize a faster mean-time-to-resolution while using the efforts of fewer full-time employees.
Upgrading your SIEM solution to one that offers these ten essential features will allow your organization to keep up with today’s expanding threat landscape—without the growing costs of highly-skilled security analysts and outdated log volume and pricing models.
Learn more: For an in-depth view, see the Exabeam webinar, 10 Must-Have Features of a Modern SIEM.
See Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.
Log Management
Authored by Exabeam
- What Is Log Management? Process & Tools
- 7 Critical Log Management Best Practices
- 5 Best Log Analysis Tools You Should Know in 2023
Security Operations Center
Authored by Exabeam
- SOC Analyst: Job Description, Skills, and Certifications
- What Is a Security Operations Center? Complete Guide
- 5 SecOps Functions and Best Practices for SecOps Success
Disaster Recovery
Authored by Cloudian






