Cloud-scale Security Log Management
Cloud-native solution to ingest, parse, store, and search log data at scale. Rapid data ingestion with hyper-quick query performance, with dashboards and reporting, and lightning-fast, modern search across multi-year data.
Log management designed for security
Exabeam provides your organization with affordable security log management at scale without requiring advanced programming or query-building skills. Ingest, parse, store, and search security data in one place.


Collectors
A single interface is used to securely configure, manage, and monitor the transport of data into the Exabeam service at scale from on-premises, cloud, and context sources. The platform provides collection from 200+ on-premises products through a variety of transport methods including APIs, agents, syslog, and log aggregators, such as SIEM or log management products. To meet the increasing need for cloud security and cloud data collection, Exabeam supports 34 cloud-delivered security products, 11 SaaS productivity applications, and 21 cloud infrastructure products from the three leading cloud infrastructure providers. For context, the platform supports the collection of threat intelligence feeds, geolocation data, user, and asset details.
Log stream
Delivers rapid log ingestion processing at a sustained rate of over 1M EPS. A central console enables you to visualize, create, deploy, and monitor parsers within a unified ingestion pipeline for all Exabeam products and features. As it is ingested, data is parsed using 7,937 pre-built log parsers and enriched using context sources from open source and commercial threat intelligence feeds. Enriched, parsed data is available as security-relevant events for faster performance in search, correlations, and dashboards. Live Tail capabilities provide self-service, real-time monitoring of parser performance, and visibility into the data pipeline. This provides the ability to take immediate action to improve the quality of data ingestion.

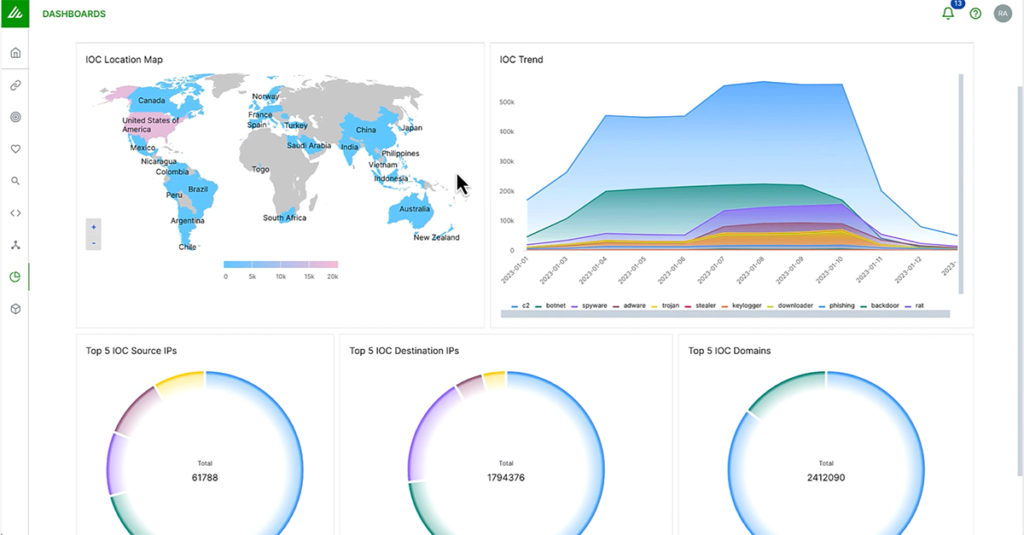
Search
Search is an essential feature of Exabeam products. Search is a single interface that allows analysts to search for events, IoCs, or Exabeam-generated anomalies. The time savings is particularly valuable as investigations usually entail multiple queries and require that search terms be refined over multiple iterations to obtain the desired results. Analysts no longer have to wait hours to get search results from network attached storage (NAS) or other offline storage. Searching across real-time or historical data is no longer a barrier — security operations teams do not have to import and wait for historical data to be restored and processed.
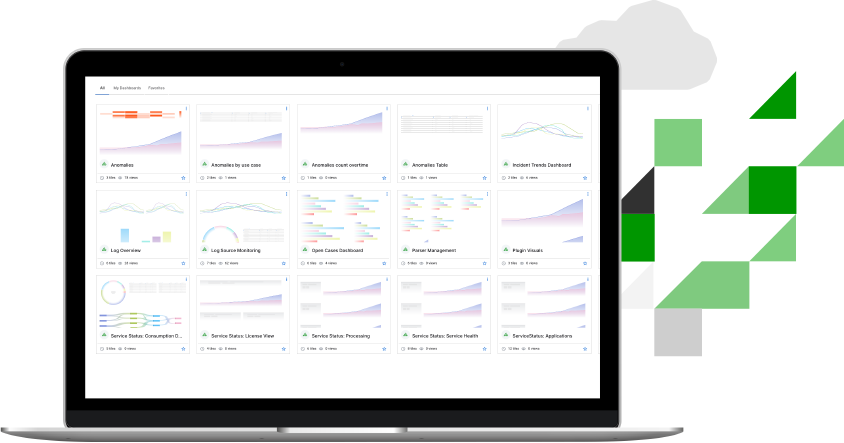
Reporting and dashboards
Print, export, or view dashboard data with pre-built compliance reports, customized reports, and dashboards with 14 different chart types.
Build a dashboard in a minute from 14 different pre-built chart types as if you were using a leading BI tool. The Exabeam dashboard app is fully integrated within Exabeam products, allowing you to create powerful visualizations from your parsed log data quickly. Customers can choose one or more visuals to meet their business needs. These include bar chart, column chart, line graph, area chart, pie chart, donut chart, bubble chart, funnel, single value, sankey map, word cloud, heat map, table, and Coverage Map.

Correlation rules
Correlation Rules compare incoming events with predefined relationships between entities to identify and escalate anomalies. A single interface lets you write, test, publish, and monitor hundreds of custom correlation rules for your most critical business entities and assets, including defining higher criticality rules for advanced threats sourced from the Threat Intelligence Service (available at no additional cost).
Properly designed correlation rules enable enterprises to surface a broad range of abnormal behavior and events. Correlation Rules provides analysts with an easy application to create custom correlation rules suited to their organization’s security and use case requirements.
vendor integrations
Collect data from more than 680 different product integrations across 350+ different vendors.
events per second
Rapid log ingestion processing at a sustained rate of over 2M EPS.
pre-built compliance dashboards
Build a dashboard in a minute from 14 different pre-built chart types as if you were using a leading BI tool.
Frequently Asked Questions
Answer: Exabeam is a security company — our products are built for security people by security people. The security products we provide offer multiple capabilities including data collection, threat detection, incident investigation, and response automation to achieve outcomes based on use cases. Prescriptive workflows and guided checklists help teams quickly operationalize their Exabeam deployment. The components are built following security best practices and with the highest security standards.
With Exabeam Security Log Management and Exabeam SIEM, all ingested logs, events and sessions are stored and available for search, visualization, and investigations for 30 days with extensions up to ten years available for purchase.
Answer: All your data is protected through an end-to-end encryption data flow pipeline. We start by ingesting logs and data from APIs and Exabeam Collectors using secure communication channels (Syslog, agents, Kafka sources using SSL/TLS) in your environment and then upload them through TLS-secured channels onto the cloud-native Exabeam Security Operations Platform. In addition, Exabeam encrypts data at rest to ensure the highest level of security for your data. Exabeam is SOC2 Type II certified. To meet the requirements for certification we have developed and follow strict information security procedures and policies for the security, availability, processing, integrity, confidentiality, and privacy of customer data. This aligns with Exabeam’s ongoing commitment to create and maintain a secure operating environment for our clients’ data.
Trusted by organizations
around the world





















“We’re generating event logs across hundreds of systems and that’s getting sent to a central location, and with Exabeam, it was so easy just to tie that central location and send all that data to Exabeam. So that was one of our key requirements. And it was definitely easier with Exabeam than a lot of the other solutions we tried.”
Zane Gittins
IT Security Specialist | Meissner Filtration

Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.

GUIDE
7 Best Practices for Secure Enterprise Log Management
Learn what enterprises should insist on when considering log management solutions for today’s hyperscale cloud and hybrid world, including seven best practices and how Exabeam can help your organization achieve better security outcomes.
What else can Exabeam do for you?
At Exabeam, we deliver persona-based workflows, purpose-built for security. With support resources, professional services, training opportunities, and business partnerships, Exabeam can usher your organization through deployment and beyond.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision