Compromised Insiders
Detect and mitigate insiders who are knowing or unknowingly carrying out an attack.
Trusted by organizations
around the world





















What if attackers can just log in?
If an attacker gains access to valid user credentials it becomes very simple to carry out a successful attack. The end result – massive data breaches and even more costly recovery.
- Compromised Credentials
- Lateral Movement
- Privilege Escalation
- Privileged Activity
- Account Manipulation
- Data Exfiltration
- Evasion
Exabeam helps security teams detect compromised credentials by applying machine learning and user behavior analysis to baseline normal behavior for every user, device, and peer group.
Exabeam then automatically detects anomalous behaviors that are indicative of a compromised account, regardless of the attackers’ techniques.
Using specific data Exabeam enables analysts to see risky access and attacker techniques, like pass the hash, pass the ticket, and more.
Exabeam behavioral models put anomalous activity, like first time or failed access to hosts and assets in the context of the historical behavior of that user, their peers, and their organization to clearly identify attacker behavior from normal activity.
Privilege escalation can enable access to high-value assets without restriction.
Exabeam mitigates attackers’ privilege escalation by detecting techniques like credential enumeration, bloodhound execution, and more.
Behavioral models detect anomalous activity, like first-time access to hosts and assets or permission changes, and put them in the context of the historical behavior of that user, their peers, and their organization to clearly distinguish an attacker from a normal user.
Attackers target privileged accounts to bypass security controls and monitoring, disrupt corporate operations, or exfiltrate large amounts of sensitive data.
Exabeam detects attackers performing privileged activity through the combination of user context and identification of abnormal behavior.
Exabeam detects account manipulation by identifying abnormal user behavior such as manipulating an organization’s active directory (AD), creating or deleting accounts, or modifying group membership and permissions.
Exabeam also detects unusual activity performed by attackers, like when they hide behind system accounts, or when there is an abnormal activity using a non-service account.
Exabeam puts DLP alerts in the context of a user’s normal behavior to better identify when they pertain to a compromised user. By combining user activity from a variety of data sources, including those from DLP tools, Exabeam can detect data exfiltration across a variety of channels, including domain name system (DNS), email, or web upload.
Exabeam detects anomalous activity associated with evasions, such as tampering with audit logs, file destruction or encryption, and the use of a tor proxy to hide web activity.
of breaches
Percentage of breaches involving compromised credentials.
MITRE ATT&CK® categories
Coverage for all ATT&CK categories, including 199 techniques and 379 sub-techniques.
anomaly rules
Over 1,800 anomaly rules, including cloud infrastructure security, with over 795 behavioral models that automatically baseline normal behavior of users and devices.
1 The combined reduction organizations achieved in a recent study.
Explore the many ways Exabeam can work for you
Whether you replace a legacy SIEM, or complement an ineffective SIEM solution by adding UEBA, automation, and TDIR content on top, the modular Exabeam Security Operations Platform can help you achieve security operations success.
- Get started: Exabeam Security Log Management
- SIEM replacement: Exabeam SIEM and Exabeam Fusion
- SIEM augmentation: Exabeam Security Analytics and Exabeam Security Investigation
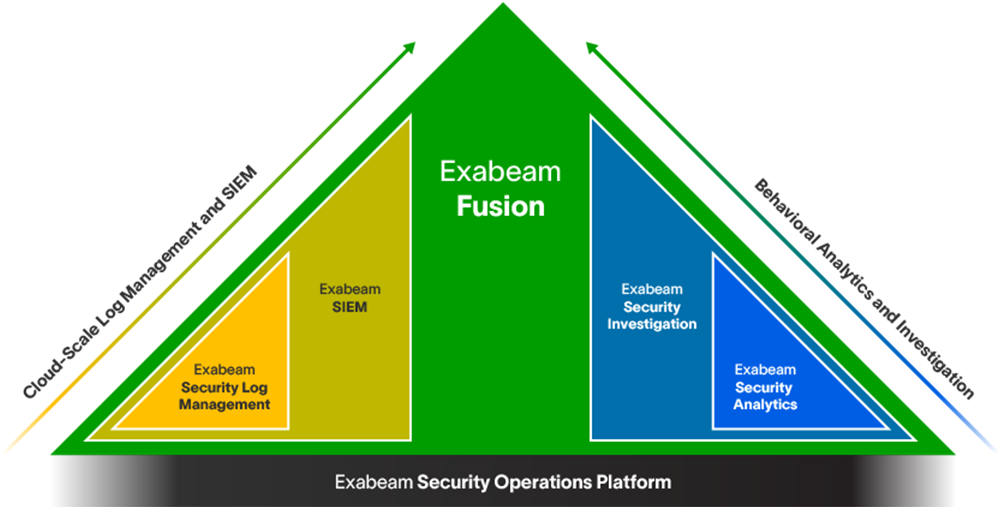
Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.

SOLUTION BRIEF
Compromised Credentials
Compromised credentials – when a legitimate user’s credentials have been unknowingly obtained by a malicious actor and used to access the corporate assets.

SOLUTION BRIEF
Lateral Movement
Lateral movement is when an attacker compromises or gains control of one asset within a network and then moves internally within a network from that device to others.

SOLUTION BRIEF
Privilege Escalation
Privilege escalation refers to an attack where
the attacker gains higher-level permissions or
unauthorized access to privileged user accounts or
assets.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision






