Two weeks after a disruptive ransomware attack almost 10,000 Baltimore city government computers remain unusable delaying home sales and payment of water bills.
Earlier another ransomware attack created a glitch for travelers at Cleveland Hopkins International Airport. Anyone interested in checking the flight status on the big screens located throughout the airport was greeted by a blank screen, a problem that persisted for multiple days.
The culprits? In each case, the outages were caused by ransomware, a form of malware that demands a “ransom” from the owner of the device affected.
How could such targeted attacks happen, and how can organizations keep it from happening to them? Let’s take a look at how a ransomware attack works.
About the Attacks
On May 7th, the city of Baltimore was hit by cyber criminals demanding an undisclosed sum to unlock computers. The ransom hasn’t been paid as of the writing of this post and the case is being investigated by the Federal Bureau of Investigation. It could take months to recover some systems says Baltimore Mayor Bernard C. Young.
On April 22nd, Cleveland Hopkins International Airport experienced a sudden outage affecting the screens used for flight and baggage information, among other operations. Although the airport’s screens were affected for several days, flights and airport security remained unaffected the entire time.
Ransomware responsible for both outages is a growing issue and is expected to cause more than $20 billion in damages by the end of 2021. Experts predict that by that time, ransomware will hit a business every 11 seconds. Instead of attacks targeting one device, ransomware is expected to expand to large-scale infections geared toward taking down entire networks. Potentially these attacks could have the power to disable systems for days or weeks, even months.
The Ransomware Kill Chain
The first step toward battling ransomware is understanding how it works. Ransomware follows the same six stages with each deployment, even with permutations and improvements to a strain. Here are the main six stages of any ransomware instance:
- Distribution– The infection starts with someone in your organization. Using techniques like social engineering and DNS weaponizing, attackers find a way to convince your users to download a file or click on a link, triggering the infection.
- Infection– Now that it’s found a way in, the software launches an executable that installs malicious code. This is the ransomware.
- Staging– Once it’s been deployed, the ransomware begins to embed itself into your system, setting itself up to remain in place even after it’s been rebooted.
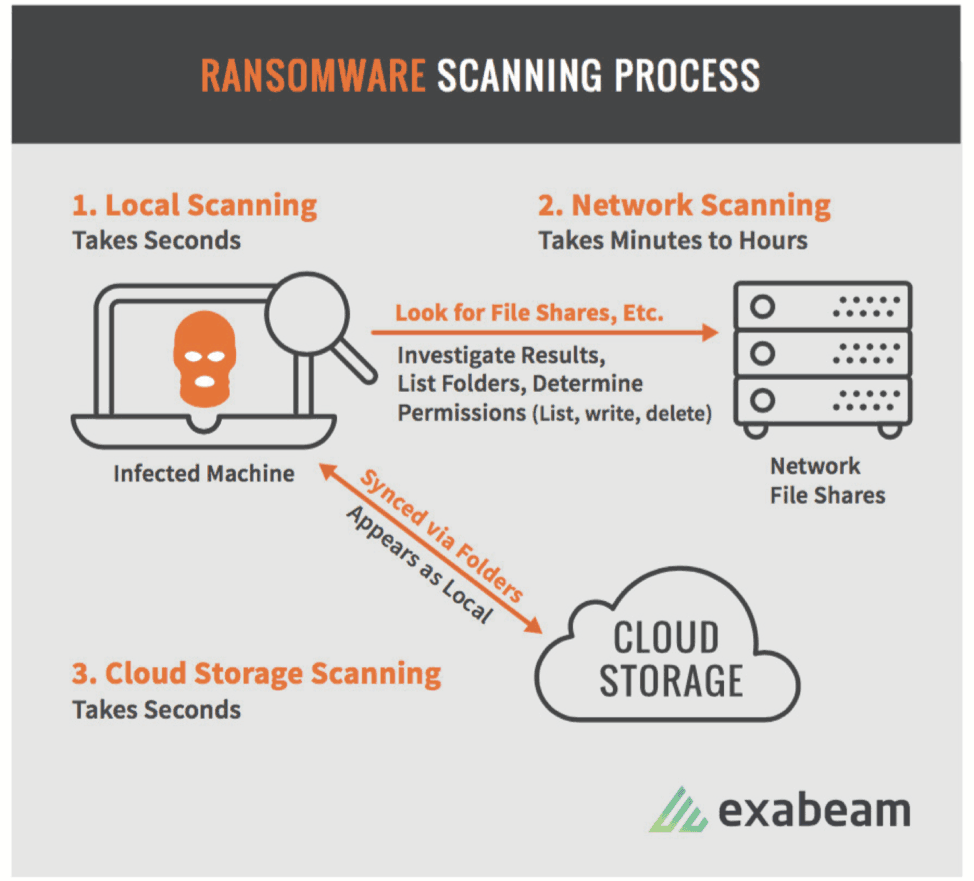
- Scanning– In this stage, the ransomware prepares for the next stage by searching both the infected device and all connected systems for content to encrypt.
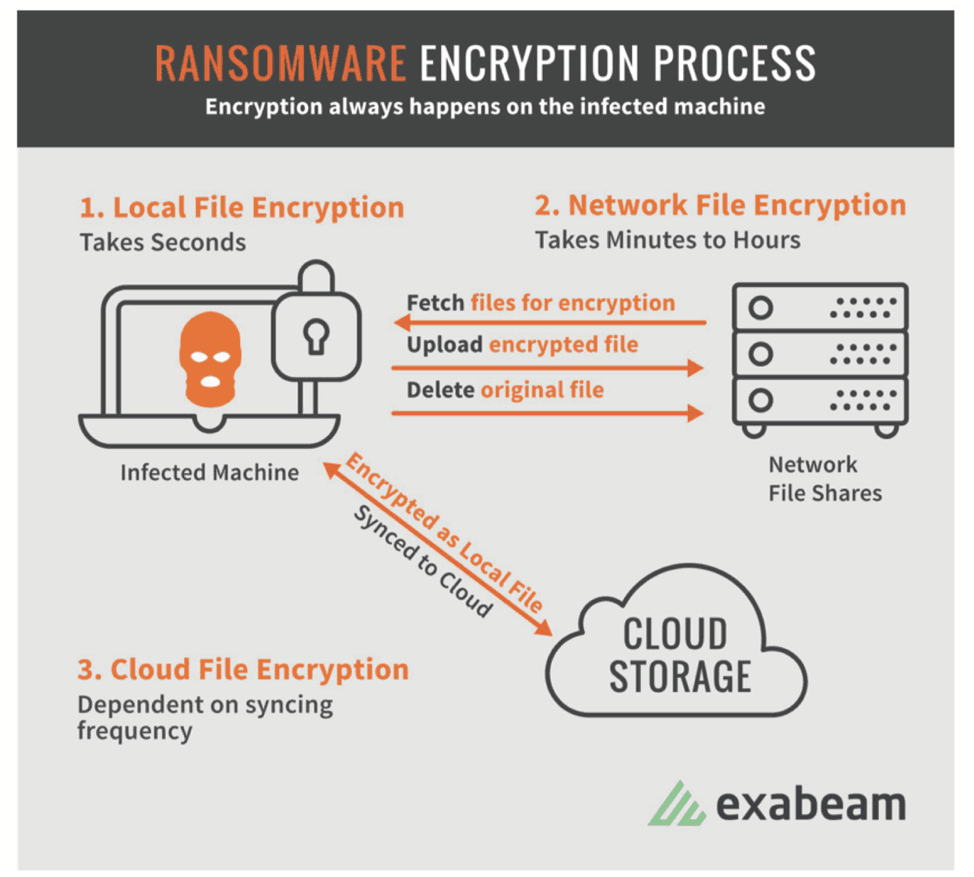
- Encryption– In order to scramble systems and cause damage, the ransomware encrypts all discovered files.
- Payday– This is the final stage, where the ransom note is presented to the victim and you take action to repair the damage and resume control of your system.
Paying ransom is never a good idea. According to one report, of those who paid the ransom, only 19 percent got their data back. Once your system is infected, you’ll often need to use specialized software to remove the threat, then restore all the files you lost from backup. All of this can take hours of work, with your systems potentially being completely down for a while until you can restore minimum functionality.
Behaviors That Are Telling
Before you can put a solution in place to keep your network safe, you’ll need to know what, specifically, you’re monitoring. Each kill-chain stage has very specific activities associated with it. Watching for those activities can help you detect an incident as it’s happening and stop it dead in its tracks.
Here are the activities generally associated with each kill-chain stage:
- Distribution– Found in an email, proxy, your firewall, or intrusion prevention system, you’ll notice strange behavior in an incoming file attached to an email.
- Infection– In process logs, you’ll see this as new activity when the code is dropped on the computer. Also look for files that were renamed or run from somewhere suspicious, such as a temp directory. You may also see this as a process that runs another process, then vanishes. Look for this in the proxy or process tracking, and also watch file activity.
- Staging– At this point, the ransomware is making its way into your system, so you may see an executable created by a process not previously seen in your enterprise. Also watch your registry for signs that something has added an autorun entry. Look for signs that boot options have been modified through a command prompt or a process has uploaded information to a domain that was recently registered.
- Scanning– As the ransomware scans for data to encrypt, you’ll see signs in your authentication logs that this is taking place.
- Encryption– At this point, the ransomware begins working hard, so you may see processes reading, creating, and deleting files from a large number of directories in a short timeframe. Also look for newly-created files with unusual extensions. If a process has created files in small numbers, scattered across a large number of directories, this could also be a sign your system is under attack.
- Payday– Once the ransomware has completed its encryption, you’ll see odd things like desktop backgrounds being changed or web browsers being launched at random.
Using Behavioral Modeling to Detect Threats
By the time you realize your system is infected, it’s already too late. These attacks are so sophisticated, they can be difficult to prevent, especially since infections usually disguise themselves as innocent attachments or email links. You can educate your end users, but there’s no guarantee someone won’t eventually make a mistake.
The biggest problem with detecting ransomware is that it’s designed to avoid traditional threat detection processes. Ransomware updates constantly—at least once every 24 hours. Antivirus vendors and malware detection solutions can’t keep up with these threats because, by the time they’re known, they’re already obsolete.
Since these traditional approaches to detection are ineffective, security teams must rely on other approaches. One of the best ways to do this is through the use of behavioral modeling, which involves using all available data to predict future behavior. By looking at the ransomware kill-chain’s progression of distribution, infection, staging, scanning, encryption, and payday, you can begin to see signs in your own file activity logs, registry tracking logs, and security alerts.
The best thing about ransomware is that it has to make it all the way from the first step in the chain to the last step in order to successfully take over a system. If you can catch it at any stage of the cycle, you can stop it dead in its tracks. The goal is to monitor for certain behaviors on a regular basis and familiarize yourself with normal behavior for users and devices on your network. By fully understanding what’s normal, you’ll be able to more quickly detect when something unusual takes place.
Manually monitoring systems is time-consuming and prone to human error. It’s impractical for security analysts to monitor every system and device in your network 24 hours a day, 365 days a year. With the right threat detection system in place, businesses can automate these processes so that solutions are constantly monitoring for certain behavioral abnormalities.
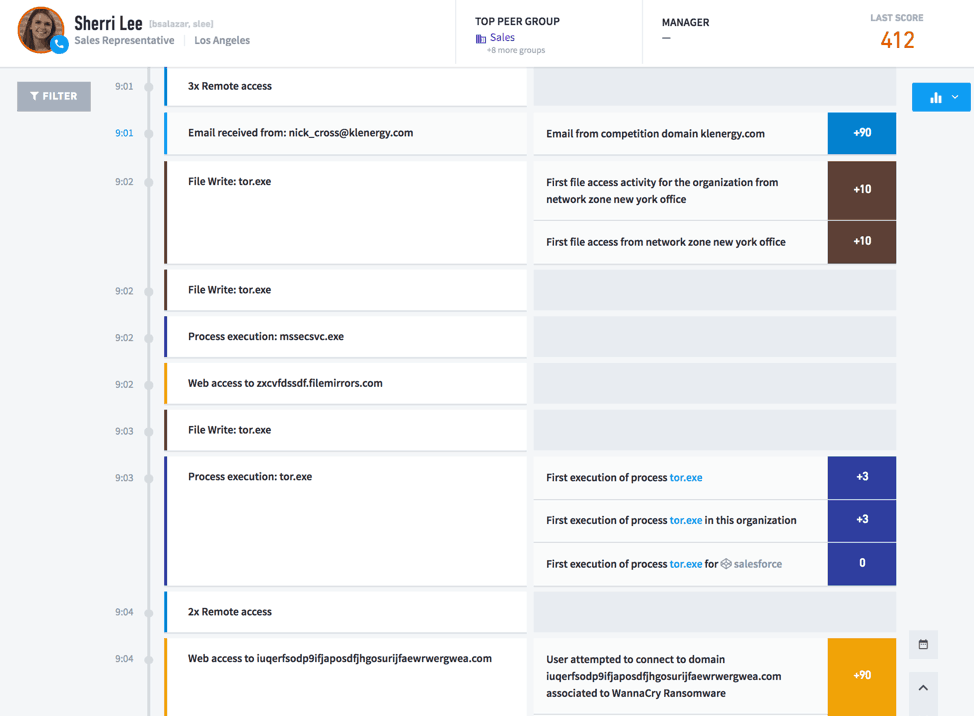
Figure 1: An example of the Exabeam Smart Timeline showing ransomware detection with various events stitched together into a timeline before a ransomware attack. Anomalous events detected are part of distribution, infection and staging kill-chain as defined above.
The right solution can detect an attack in progress and stop it before it can take over your system. However, your security team also needs to know how ransomware works from the first stage to the last. In doing so, they’ll know exactly what to look for when their security software returns unusual activity.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!